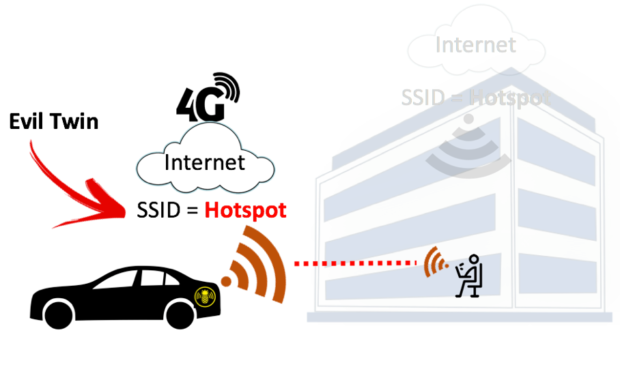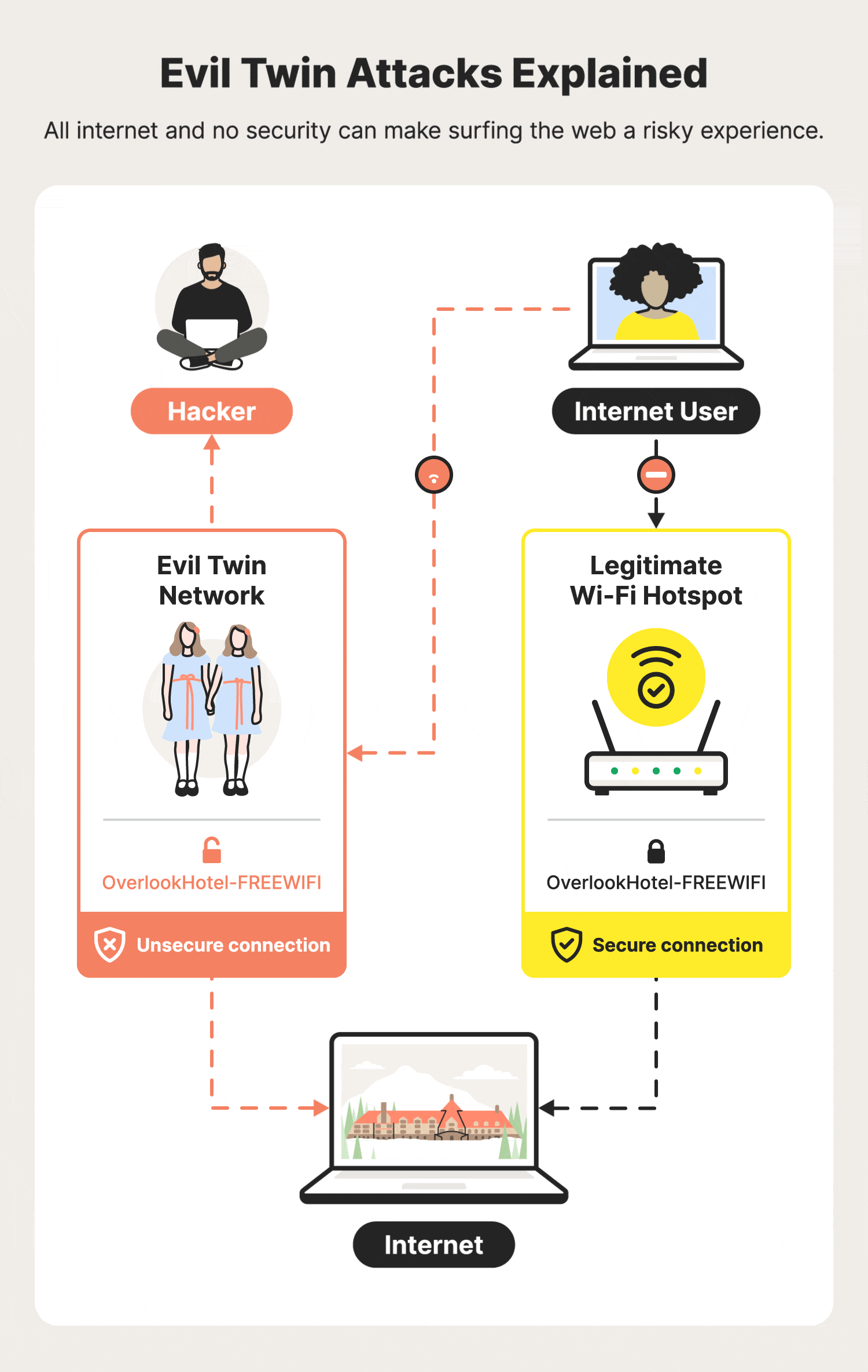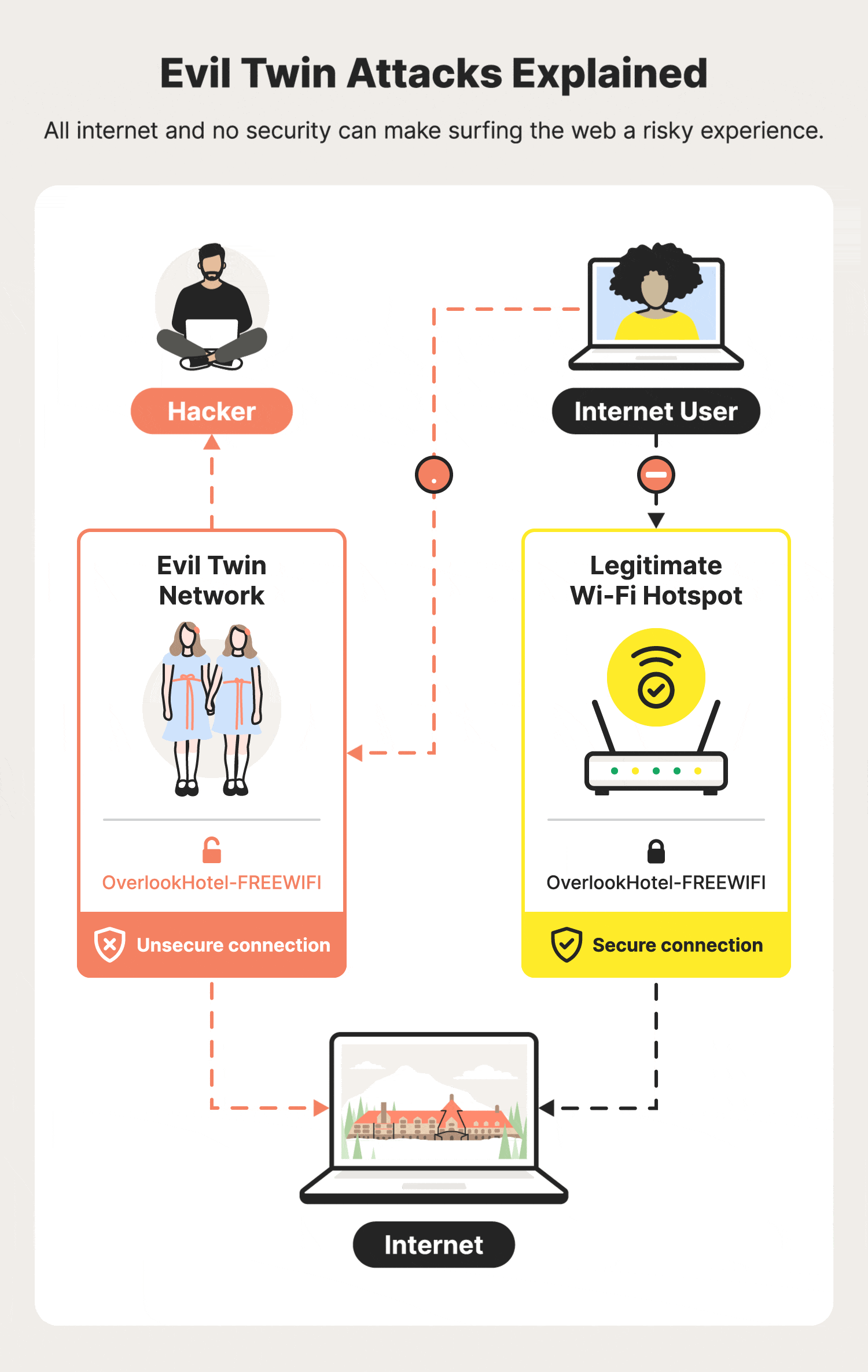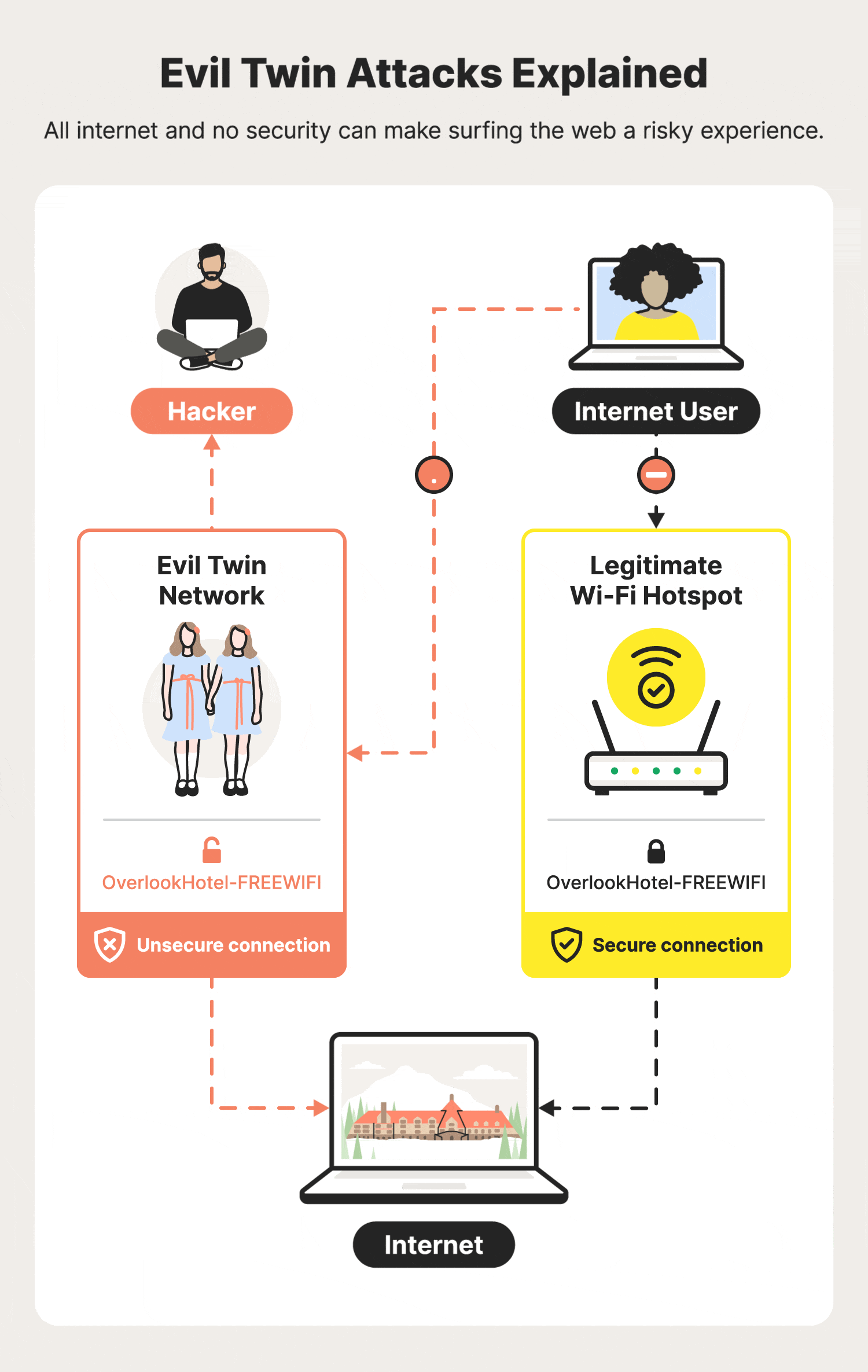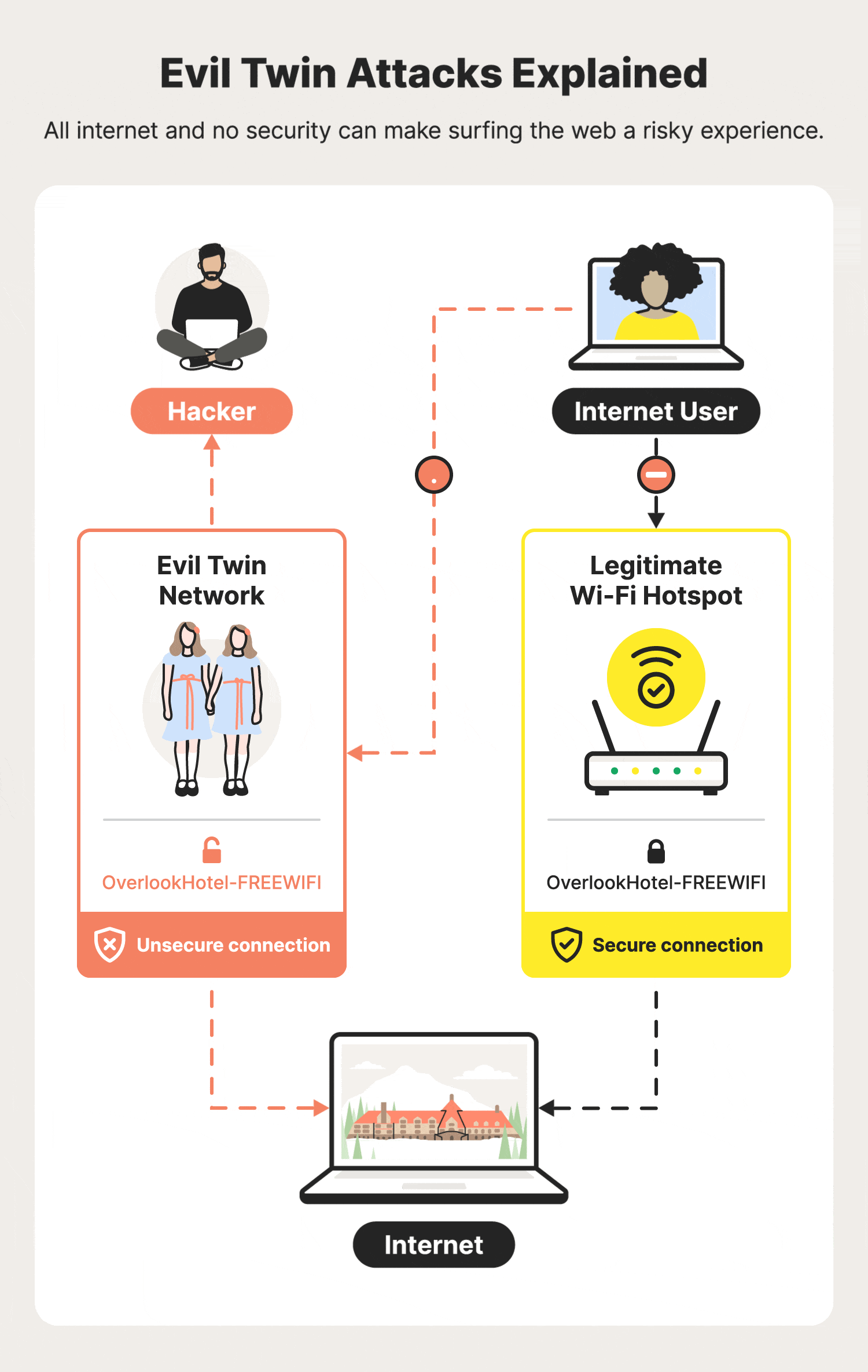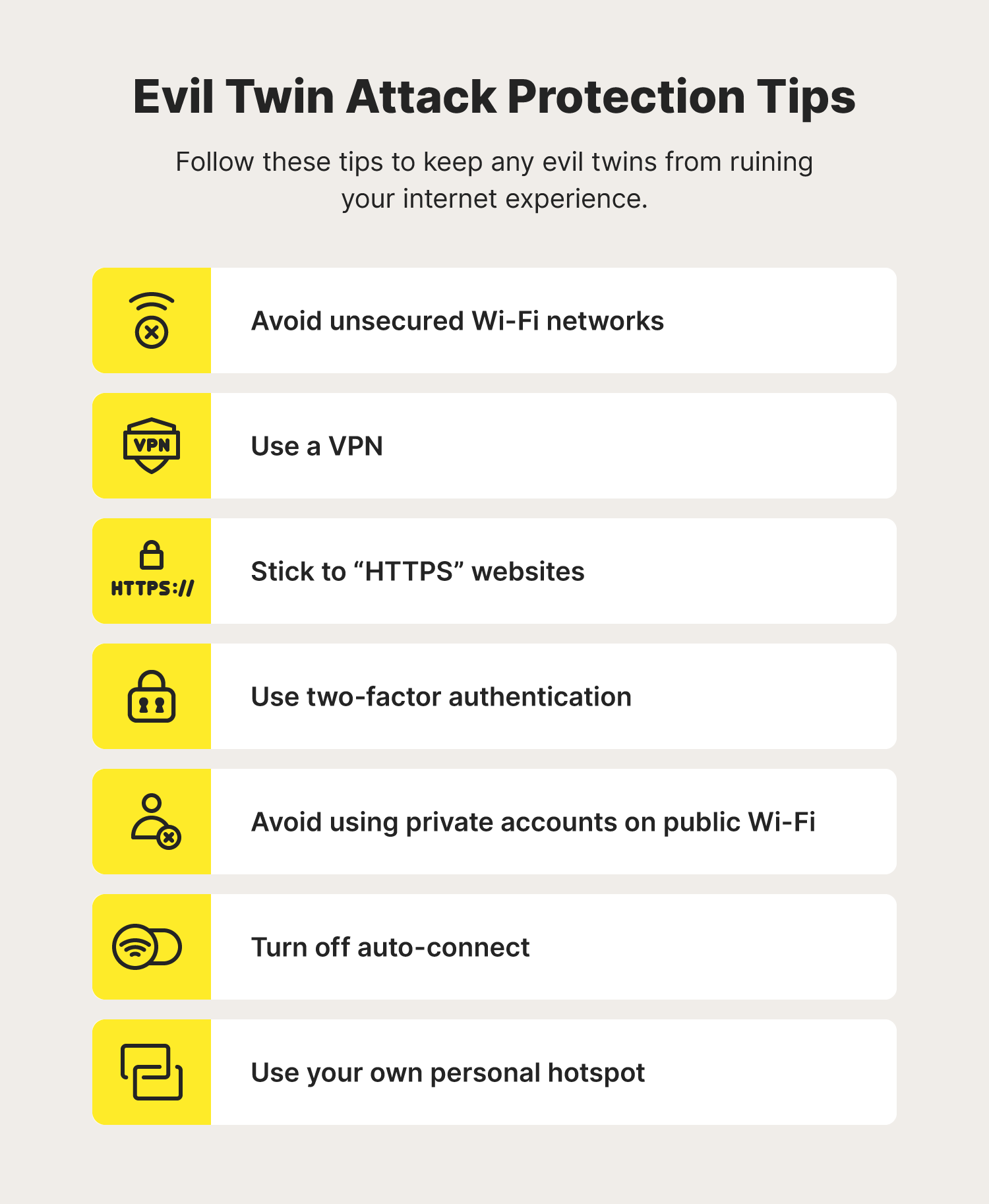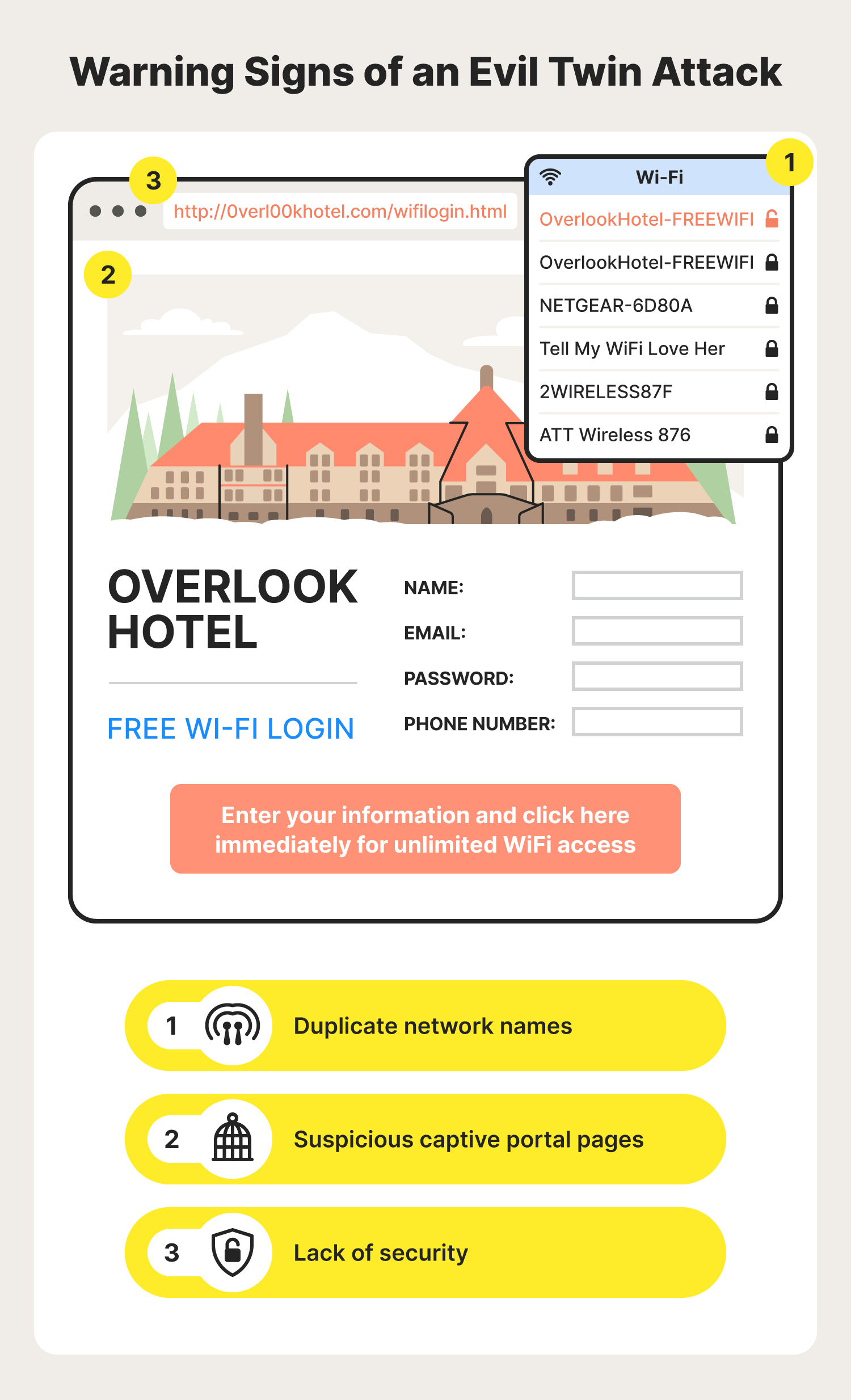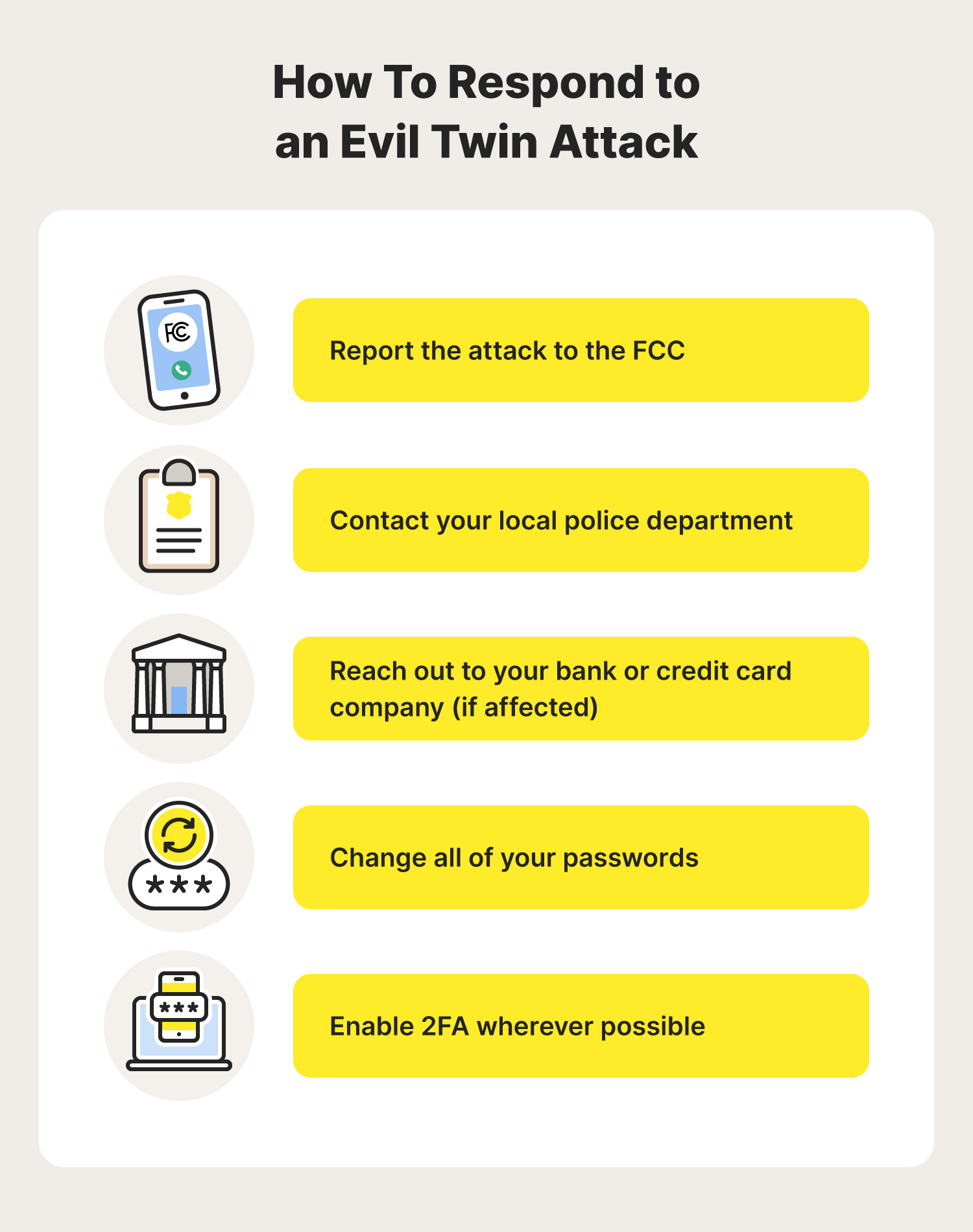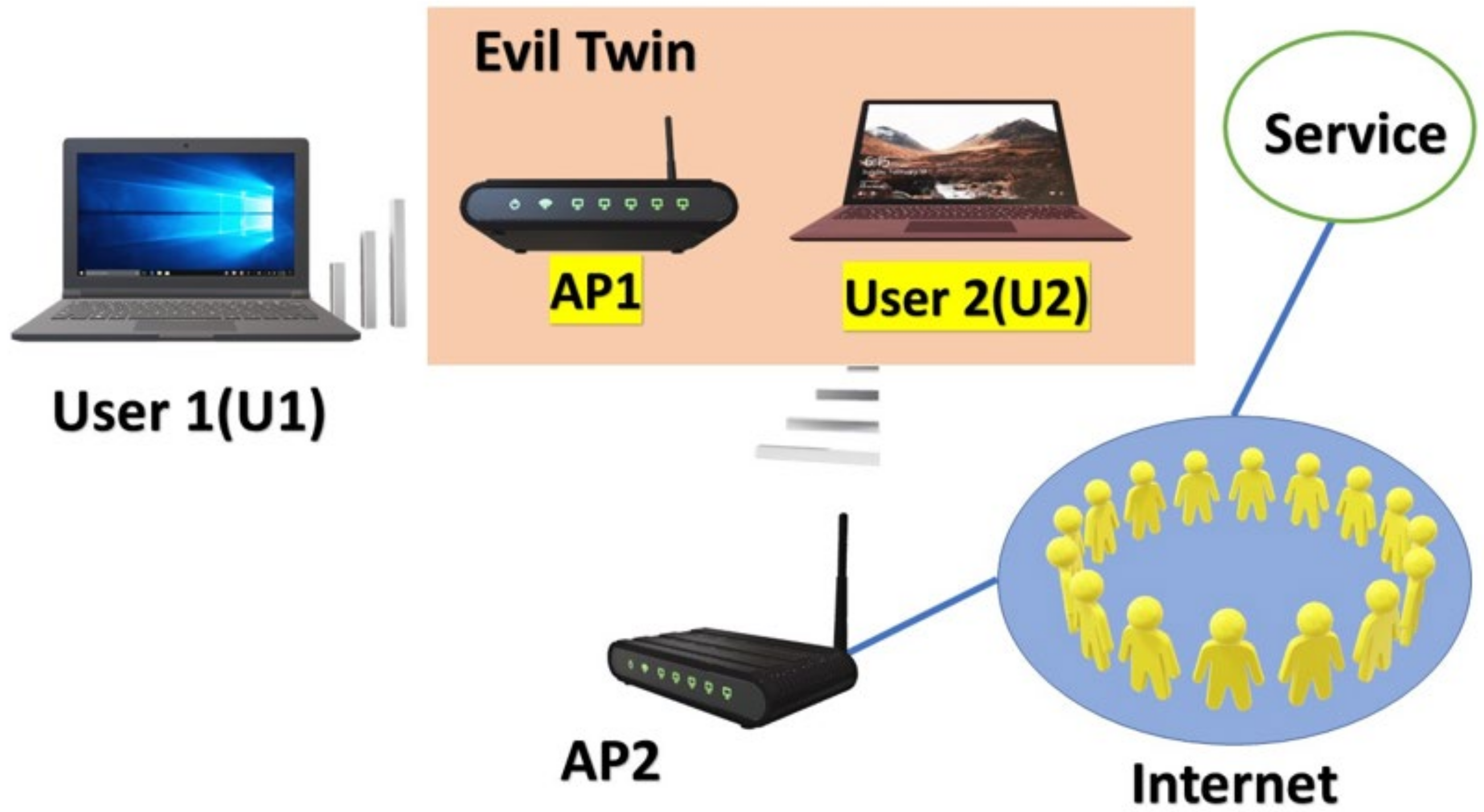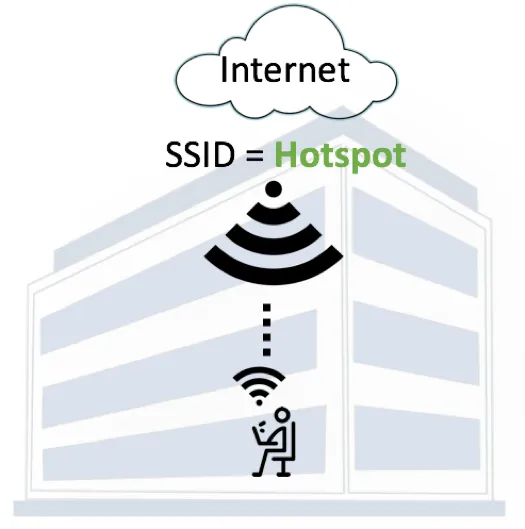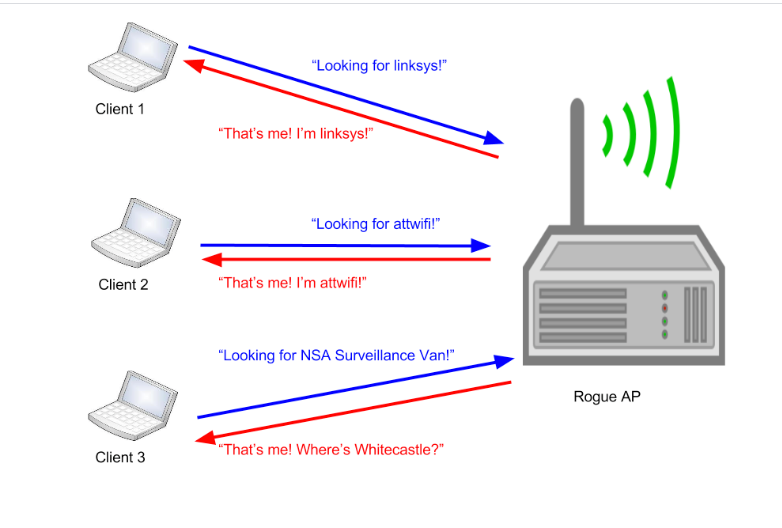
Modern Wireless Tradecraft Pt I — Basic Rogue AP Theory — Evil Twin and Karma Attacks | by Gabriel Ryan | Posts By SpecterOps Team Members

Gateway independent user-side wi-fi Evil Twin Attack detection using virtual wireless clients - ScienceDirect